Congratulations! You have won a trip to Tahiti! Click to claim your prize!!
Anyone who has ever used the internet has seen messages like this one. Hackers and thieves send them as bait to lure unsuspecting users into revealing personal information or downloading malicious programs onto their computers. The technique is commonly referred to as “phishing.”
Being vigilant for phishing attempts is one of the first skills we all develop when using the internet. You and your employees are probably pretty good at it already. But phishing attacks come in many forms, and even internet-savvy users fall victim.
How can you best protect your employees and your business? Here are three examples of common attacks to show your employees, so they become extra vigilant.
1. Requests for Help
REQUEST FOR URGENT BUSINESS RELATIONSHIP
[…]WE ARE TOP OFFICIAL OF THE FEDERAL GOVERNMENT CONTRACT REVIEW PANEL WHO ARE INTERESTED IN IMPORATION OF GOODS INTO OUR COUNTRY WITH FUNDS WHICH ARE PRESENTLY TRAPPED IN NIGERIA. IN ORDER TO COMMENCE THIS BUSINESS WE SOLICIT YOUR ASSISTANCE TO ENABLE US TRANSFER INTO YOUR ACCOUNT THE SAID TRAPPED FUNDS.
[...]I HAVE THEREFORE, BEEN DELEGATED AS A MATTER OF TRUST BY MY COLLEAGUES OF THE PANEL TO LOOK FOR AN OVERSEAS PARTNER INTO WHOSE ACCOUNT WE WOULD TRANSFER THE SUM OF US$21,320,000.00(TWENTY ONE MILLION, THREE HUNDRED AND TWENTY THOUSAND U.S DOLLARS). HENCE WE ARE WRITING YOU THIS LETTER.
WE HAVE AGREED TO SHARE THE MONEY THUS; 1. 20% FOR THE ACCOUNT OWNER 2. 70% FOR US (THE OFFICIALS) 3. 10% TO BE USED IN SETTLING TAXATION AND ALL LOCAL AND FOREIGN EXPENSES. IT IS FROM THE 70% THAT WE WISH TO COMMENCE THE IMPORTATION BUSINESS.
[...]WE ARE LOOKING FORWARD TO DOING THIS BUSINESS WITH YOU AND SOLICIT YOUR CONFIDENTIALITY IN THIS TRANSATION. PLEASE ACKNOWLEDGE THE RECEIPT OF THIS LETTER USING THE ABOVE TEL/FAX NUMBERS. I WILL SEND YOU DETAILED INFORMATION OF THIS
PENDING PROJECT WHEN I HAVE HEARD FROM YOU.
YOURS FAITHFULLY,
DR CLEMENT OKON
NOTE; PLEASE QUOTE THIS REFERENCE NUMBER (VE/S/09/99) IN ALL YOUR RESPONSES.
This is an example of the so-called “Nigerian Scam.” These messages masquerade as pleas for help from foreign representatives, who ask to use your bank account to move large sums of money. In exchange, they offer to reward you with a small percentage of that money.
These scams have been around since before the internet, but they’re still used today because they work. The appeal of “free” money, combined with the notion of helping someone in need, has allowed scams like these to swindle people for decades.
PRO TIP: It sounds obvious, but if it's too good to be true, it probably is. And any international correspondence from an unexpected person/address should get extra scrutiny.
Security Alerts
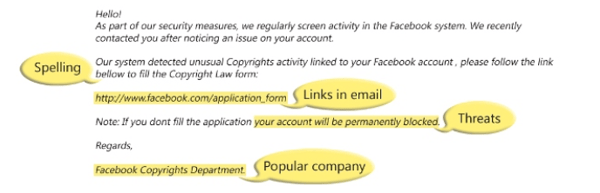
This example from Microsoft is a phishing attack disguised as an official message from Facebook. Because Facebook is so prevalent, the attackers can safely assume their targets probably have an account. Scams like this one are successful by pretending to be a friendly security message and by threatening to close the target’s account if no action is taken.
PRO TIP: Hover over (but don't click on) the suspicious link. If the window that pops up shows a different, non-company URL, you've probably discovered a scam.
Unexpected Official-Looking Messages
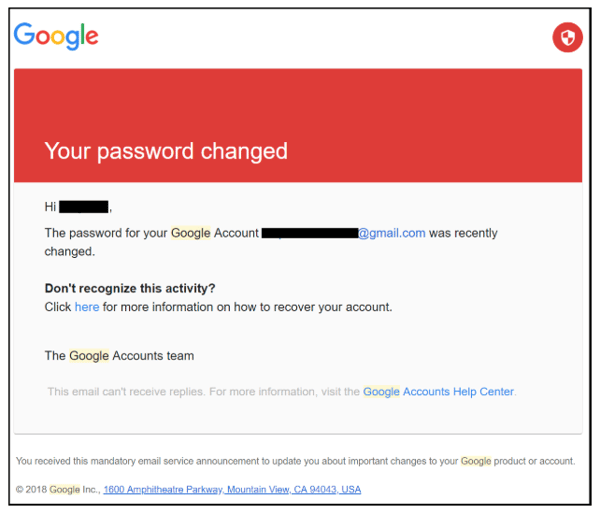
The first two examples had some obvious clues that they were scams. However, this example is an exact copy of a actual, official email from Google. Attackers can copy official emails like this one and replace the “click here” link with a website designed to steal your data or infect your system.
These are the most dangerous phishing attacks, because there are no obvious clues that something is amiss. Be cautious around messages about your accounts that you aren’t expecting. They could be warning you of someone trying to log in to your account, but they could also be phishing attacks themselves.
PRO TIP: The best way to authenticate an email that claims to be from Gmail is to trace its full header. Also, beware that Google will never ask for personal information like a password via email.
Best Practices for Phishing Scams
So what should an employee do if they’ve received an email that they suspect is a phishing attack?
- Don’t open it. Spam emails can contain malicious links or viruses that will trigger additional attacks, simply by being opened.
- Notify IT. Your IT security team can investigate whether other employees have received the message and can prepare your network for possible repercussions.
- Delete the email. After notifying IT of the message, delete it. You don’t want to risk accidentally opening it again later.
A chain is only as strong as its weakest link. If even one person falls prey to a phishing attempt, your entire network could be at risk.

