We log into multiple accounts every day: emails, social media, shopping platforms and bank or financial accounts. The rise of remote or hybrid workplaces means that at-home employees must access the company’s work system and perform tasks.
Most of these accounts store sensitive data like personal or financial information, which needs protection from cyber attacks. Although usernames and passwords initially protect all accounts, this information can be vulnerable to hackers.
If you’re looking for a way to thwart hackers and improve security, it's important to implement two-factor verification.
Watch Now: Essential Elements of Cybersecurity and Cyber Insurance Webinar
 What Is Two-Factor Verification?
What Is Two-Factor Verification?
Two-factor verification, or 2FA, is a type of multi-factor authentication that requires two methods, or authentication factors, to verify your identity when you attempt to log in to an account. Basically, the user is trying to prove they are who they claim to be so they can access the account.
2FA, which is sometimes two-step verification, or 2SV, is a way of preventing unauthorized users from accessing an account or system – only trusted users and devices can log in. This helps businesses safeguard valuable information and networks, including employee and client privacy and data.
The way 2FA works is that you first log in to your account with your username and password. You then must verify who you are with an extra factor. It’s this second factor that makes it difficult for hackers to access your account – if they’re unsuccessful, they are denied access.
How Does Two-Factor Authentication Fight Hacks?
Password-based authentication is no longer enough to protect your business. Cybercriminals are constantly developing new ways to steal or guess passwords to then hack into systems. They use phishing attacks, stolen credentials, social engineering, brute-force attacks, keylogging or credential exploitation. They attack businesses of all types and sizes.
And once they hack into an account, they cause absolute chaos – all your information is right there for them, not to mention your clients’ information. Hackers can steal, destroy or sell this information, causing further damage. In 2022, the average total cost of data breaches was$4.35 million, and it can sometimes take months to secure your company again.
That’s why 2FA is a great way to add an extra layer of protection and security from hackers and cyber attacks so you can maintain your productivity and reputation: even if a hacker does get your username and password, they now need that second factor to access your account.

Types of Two-Factor Authentication
There are several types of two-factor authentication factors to verify a user’s identity, but you only need two for successful verification.
1. Knowledge factor – this is information that the user would know, like a password, a PIN or an answer to a security question. This is usually the first type of factor.
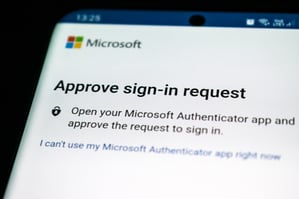
2. Possession factor – this is something the user would possess, like a smart card, a badge, a USB device or a physical security fob, token or key. Authenticator apps likeAuthy,Duo or Microsoft Authentication would also fall under this category. Most of these generate a one-time password (OTP) that is usually six digits and sent via text, email or phone call. Authenticators usually require a push notification – you simply approve or deny the login attempt. The possession factor is the second most common type.
3. Inherence factor – this is a physical attribute that belongs to a user. Often called biometrics, this includes fingerprints, retina or iris scans and face or voice recognition. You usually see these factors associated with businesses with high levels of security, like banks, government agencies or healthcare facilities.
There are also adaptive or risk-based authentication factors. These look at context or behavior to determine if a second factor is needed for a login. For example, this factor will look at when the user is trying to log in, what device is being used or the geo location of the login attempt. If a company has set work hours, only accepts access from laptops or doesn’t allow access from outside the country, someone trying to log in internationally after hours or with a phone would trigger an additional authentication factor.
Are There Risks with Two-Factor Authentication?
Although 2FA does create an extra layer of validation and helps reduce the chances of a security breach, there is no such thing as a foolproof method against cyber attacks. There are some tricks you should be aware of when you use 2FA.
If your second verification involves sending an OTP to your phone or email, keep in mind that if a hacker already has access to your phone or email, you haven’t really foiled their efforts. You always take a risk when your primary and secondary authentication are on the same channel.
That’s why push notifications through authenticator apps or physical keys are the best types of factors – physical tokens need to be on your person, and authenticator apps have you simply push a button through the app. Authenticator apps also let you sign up for notifications if someone does try to access your account. Notifications usually include the date and time of the attempt, as well as the location and device being used.
If your business relies on 2FA, make sure all your employees are properly trained in how to use it.
Two-Factor Authentication in the Modern Era
As mentioned, more and more workplaces are transitioning to hybrid or remote workplaces, so they need to ensure their data and networks are protected. Employees need to know they can work without a security hazard. Broadcasting to clients that you use 2FA is a way to gain credibility and trust with them, too.
More websites, apps and games are also utilizing 2FA as part of their login processes to protect users, including Google, MicrosoftandApple.
Don’t let cybercriminals affect you – at Thriveon, our IT professionals can monitor your systems and ensure you’re well protected. Schedule a consultation today to learn how we can protect your business from cybercriminals.

